Вебинары
Просмотреть вебинар
Fighting Ransomware
Fighting ransomware is not futile. Like any other security threat, there is a formula to understanding it and protecting against it. Although ransomware’s consequences such as data loss and unknown exposures are serious, managing this threat doesn’t have to be challenging.
In this webinar, independent information security consultant, professional speaker, and writer of numerous security books, including Hacking For Dummies, Kevin Beaver, will share his thoughts and ideas on the best ways to protect your environment – and your data – so that these criminal hackers don’t get their way. It’s simple but it requires discipline. Tune-in to see what you can do to improve your odds of ransomware success and your overall information security program.
Understanding the Depth of the Ransomware Problem in EMEA
Ransomware continues to be a major problem—and the problem is only getting worse. Malwarebytes conducted an exclusive survey with Osterman Research asking 575 organizations worldwide how ransomware is impacting their business. The responses were sobering. Ransomware is a “top three” problem for the organizations, cited by 70 percent of those surveyed. Yet most organizations are not confident in their ability to stop ransomware attacks.
Key takeaways:
- The impacts of ransomware
- How organizations are responding to ransomware
- The importance of addressing the ransomware problem
Speakers:
Michael Osterman and Dana Torgersen
Cybercrime Tactics and Techniques Q2 2017
In our third Cybercrime Tactics & Techniques report we are going to take a deep look at what threats got our attention the most during the last three months of the year and what we expect to happen moving through the next quarter.
Key takeaways include:
- Continued heavy distribution of ransomware with WannaCrypt and NotPetya making headlines
- Exploit kits remained quiet but saw some interesting developments
- Preview into Windows and Mac malware predictions for the third quarter of 2017
Speakers:
Adam Kujawa, Director of Malware Intelligence, has over 12 years of experience fighting malware on the front lines and behind the scenes. Follow Adam on Twitter @kujman5000 to stay up to date on malware intelligence.
Dana Torgersen, Sr. Product Marketing Manager, has over 10 years of InfoSec industry experience. Follow Dana on Twitter @DaToTweet for the latest news about Malwarebytes and other hot topics in cybersecurity.
Stop the Stopgaps: How to Look for New Security Technologies
Businesses have been trusting security vendors to protect their endpoints for years, but those vendors can't keep up with the speed of the evolving threat landscape. They are failing in their promise to protect their customers, and these failures have opened the door for Next-Generation Anti-Virus solutions. Desperate for relief, businesses are adding, or even replacing, their traditional AV with these NGAV solutions. And while the NGAV vendors have promised unbelievable levels of effectiveness, endpoints continue to get infected.
Given today's threat landscape, combined with so many security options available today, it can be daunting when selecting new or alternative technologies to protect your business. Your security team has unique challenges; therefore, you should be asking your next security vendor how they will meet your requirements—both for today, and the future.
Key takeaways include:
- Discuss the security landscape and current industry trends
- Peel back the hype and expose technology gaps of securitvendors
- Give Advice and best practices on selecting your next security technologies
Speakers:
David Monahan - Research Director, Enterprise Management Association
Dana Torgersen - SR. Product Marketing Manager, Malwarebytes
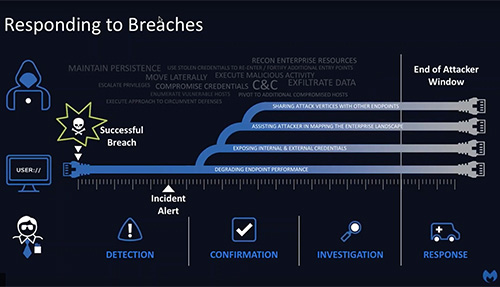
Mitigating and Responding to Ransomware
Ransomware has been around since the late 1980s but in recent years has become a much more common and disruptive element for network defenders. In this webinar, we will discuss the three types of ransomware (Client-side, Server-side and Hybrid), how to mitigate initial infection and respond to and remediate an infection with appropriate scoping, escalation and lessons learned.
In addition to technical mitigations, we will also incorporate the latest NIST guidance on recovery from destructive attacks (SP800-174), and discuss 'layer 8' strategy to obtain executive support for mitigating and recovering from a ransomware incident, which, unlike low and slow attacks on confidentiality (IP, PII, ePHI), disrupt productivity and uptime, which the business executives certainly care about in a fundamentally different way than data theft.
Speakers:
Gal Shpantzer has over 15 years of experience as an independent security professional.
Ken Liao is the Vice President of Product Marketing at Malwarebytes, with over 15 years of experience in information security.
Reducing Attacks and Improving Resiliency: The SANS 2017 Threat Hunting Survey Results | Part 2
Even though their processes aren't formal or mature, respondents reported benefits from their hunting practices, including reduce attack surfaces and detection of unknown threats in the enterprise, according to the 2016 SANS Survey on Threat Hunting. In that survey, 74% of respondents who use threat hunting said that hunting for threats reduced their attack surfaces, while 59% cited more accurate response, and 52% found previously undetected threats that were active in their enterprises. This new 2017 survey, publishing in association with the SANS Threat Hunting and Incident Response Summit, further defines how organizations apply threat hunting to enterprise response and detection, while also bringing out new best practices for integration and use of threat-hunting information. During this session, the second in a two-part series, attendees will learn about:
- Tools and skills utilized for successful hunts
- Formality of threat-hunting programs and who staffs and leads teams
- Required data feeds and collectors
- Future uses for threat hunting
- What respondents have on their wish lists
Speakers:
Dana Torgersen is a veteran product marketer who cut his teeth in network and data center security while at Secure Computing, McAfee, Palo Alto Networks, and security startup Illumio. He heads up Product Marketing for Malwarebytes, encouraging individuals and businesses to protect their endpoints against malware and exploit-based threats.
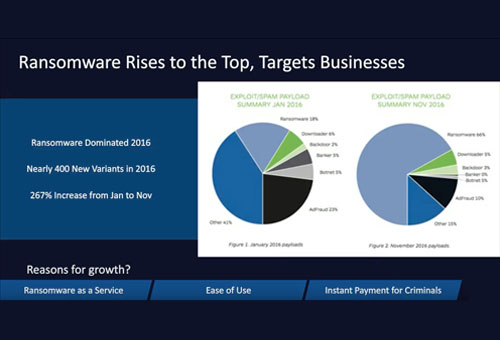
Cybercrime Tactics and Techniques Q1 2017
Overview:
In the quarterly Cybercrime Tactics and Techniques report our Malwarebytes Labs team looks deep into what is dominating the threat landscape. The Labs team specifically saw a significant shift in dominance of new threats and infection techniques in the first quarter of 2017.
Key takeaways include:
- Ransomware continued to dominate while utilized new techniques
- Exploit Kit and Malicious Spam (malspam) lead the way for distribution
- Windows and Mac malware predictions
Improving Cyber Defensive Postures | Breaches are Certain, Impact is Not
The industry is experiencing breach fatigue. Few bat an eye when we hear of the newest enterprise to be breached. Despite this understanding, the reputational and operational damages associated with breaches continue to skyrocket.
In response, enterprises are directing more resources into proactive and reactive controls which we all know don't fix the problem. Today, organizations need to rethink the concept of "protection" and shift focus from security controls to being able to detect and respond in a more agile way.
This webcast will show how enterprises can improve their cyber defensive postures and truly protect them from reputational and operational damage before, during and after an incident.
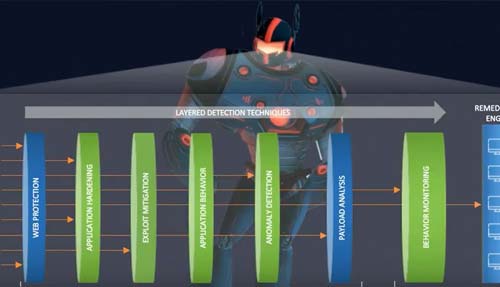
Multi-layered Security
With new threats showing up on the horizon every day, staying ahead of the curve can seem like a full-time job for IT pros. The best defense is to make sure your security solution is multi-layered.
Key topics include:
- Best practices for multi-layered security
- Protecting your data inside the perimeter: encryption, access control, SIEM etc.
- Discussing various types of threats and how to respond
2017 State of Malware
In 2016, we finally saw the headlines catch up with the hype. Cyberattacks and cybersecurity, or a lack thereof, grabbed media attention on both the corporate and consumer sides, even becoming a key issue in the US presidential election. In this respect, you could say that everyone, even those who have never logged on, was affected by cyberattacks and hacking in 2016.
Key takeaways include:
- Ransomware grabbed headlines and became the favorite attack methodology used against businesses
- Ad fraud malware, led by Kovter malware, exceeded ransomware detections at times and poses a substantial threat to consumers and businesses
- Botnets infected and recruited Internet of Things (IoT) devices to launch massive DDoS attacks
SANS Nex-Gen Endpoint Risk and Protection
Endpoints, especially user endpoints, are where most attacks get started, according to multiple SANS surveys. However, next-generation endpoint controls, while progressing, are not keeping up with the variety of devices and threats. SANS survey on next-generation endpoint risks and protections, covers how the endpoint landscape has changed in the past year and what IT security teams have done to improve their security posture. SANS explores whether or not organizations' tools and services are up to next-generation demands.
Key takeaways include:
- How organizations manage risks related to the variety of endpoints on their systems
- Respondent definitions of next-generation security
- Features users need that they're not getting with current controls
- Level of automation organizations are achieving to detect, protect and remediate
- Best practices advice from those working in the field of endpoint risks and protections
Avoid These Ransomware Mistakes
Ransomware and malware are the bane of every IT pro's existence. With new threats on the scene every day, it's practically a full time job itself to stay ahead of the curve. On this video meetup we’ll be talking with experts from Malwarebytes and an IT pro from the Spiceworks Community to find out their best tips for preventing infection, and what mistakes you could be making.
Key takeaways include:
- How to tell if your endpoint security solution is leaving gaps in your protection
- Best practices for responding to incidents
- Managing all the disparate security solutions under your roof
Combating Malvertising, Ransomware, and The Rise of Cyber Threats
According to ISACA’s 2015 Global Cybersecurity Status Report, only 38% of global organizations feel that they are prepared to handle a sophisticated cyberattack. Unsurprisingly, PWC’s “The Global State of Information Security Survey 2016” further reveals that despite the detection of a 38% increase of security incidents from 2014 to 2015, many organizations do not have the proper framework to protect themselves against cyber threats. It’s clear that in today’s relentlessly evolving digital landscape, attackers are constantly discovering new and innovative ways to infiltrate enterprise systems.
As the rise of ransomware, malvertising, and other cyber threats continue to rise, CIOS and IT leaders’ roles within the organization are rapidly evolving, as they are faced with the task of properly detecting and Combating these threats. To do this, they must continually assess questions such as: Are we aware of our top weaknesses? Are we fully briefed on the latest developments within the ransomware and malvertising space? And should a threat emerge, do we have a plan?
Speakers: Justin Dolly, Malwarebytes Steven McLean, ISO, Biomet John Newcomer, SVP Information Security, CITI Peter Rosario, ISO, USI Holdings
Malware: New Threats and Trends
The malware hitting today’s enterprises is very different from the malware they were fighting a year ago. New methods of disguise, new types of behavior, and new methods of automated malware generation mean that every day, most organizations are facing malware that is more effective, in forms that they have never seen before, in volumes that are overwhelming to current defenses. How can enterprises detect and eradicate these new threats?
In this fascinating webinar, top malware experts discuss the latest developments in malware, including new methods of obfuscation, polymorphism, and ransomware. You’ll get a look at how the most current malware behaves, and how it adapts to the environment it infects. Best of all, you’ll get insight on how to detect the latest exploits, and how to build up your anti-malware defenses to help mitigate the effects of new attacks.
Speakers: Tim Wilson, Dark Reading Editor Chief, Gal Shpantzer, Independent Security Consultant Adam Kujawa, Malwarebytes
Cybersecurity: How to Win the Big Game
All winning teams start with a game plan. When you’re captain of your IT team — you need to make a cybersecurity game plan to protect against advanced threats. Schools are prime examples of targets for evolving threats. With tight budgets, wide open campuses, and diverse endpoints — it’s no wonder attacks on schools, like ransomware, have multiplied in recent months. Despite the challenges, it’s up to IT and security professionals to gain a clear understanding of their security threats and create a winning game plan for their team.
Whether you’re an IT security professional working for an organization or an educational institution, attend this webinar to see what schools are doing to protect against cyberthreats and discover game changers you can bring to your team to create a winning cybersecurity game plan.
Listen to this webinar and you will:
- Learn solutions to prevent and remove threats
- Identify the key security threats IT teams face
- Get insight and advice from those who have addressed cybersecurity challenges
- Walk away with a game plan on how to win back control of your endpoints
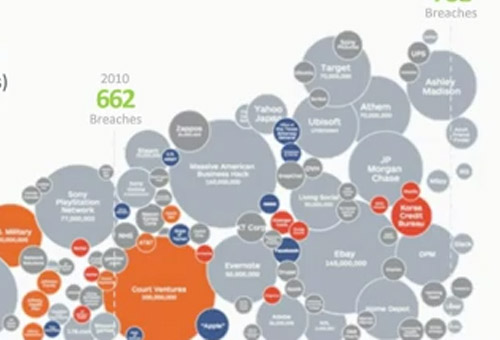
The State of Ransomware: 2016 Survey Findings
Ransomware has become one of the biggest cyber security threats in the world, with instances of ransomware in exploit kits increasing about 44% in the last six months. The business of ransomware is on pace to be a $1 billion a year crime.
Through an exclusive survey with Osterman Research of more than 500 CIOs, CISOs and IT Directors in the U.S., Canada, Germany and the U.K., Malwarebytes is dedicated to helping businesses prevent ransomware. Download this webinar and hear directly from Michael Osterman on this research.
In this webinar we will discuss:
- Most impacted industries
- Common attack vectors
- Overall impact on businesses
The Big Business of Cybercrime: New Threats and Tactics
Cybercrime is big business because it works. And because it works, it’s a growing industry attracting smart criminals. As these attacks increase in speed and sophistication, organizations need to be able to recognize the patterns and disarm the threat within seconds before your company data is held hostage. Attend this webinar to learn where the threat landscape is headed and gain insight into what steps you should be considering to counter it.
Key takeaways include:
- Identifying potential risks from ads on trusted websites
- Recognizing mobile / desktop Ransomware and how to protect against it
- How to tell if your CEO is being spoofed
Ransomware & Malvertising: Dominating the Threat Landscape
Malvertising is becoming more sophisticated and prevalent--and is the vehicle of choice for injecting ransomware.
As these attacks increase, you need to be able to recognize the patterns and disarm the threat within seconds before your company data is held hostage.
Better understand of the impact of malvertising and ransomware. Learn some of the biggest misconceptions, and see how these attacks are delivered and why your company may be at risk--without you even knowing it.
Key takeaways include:
- The growth in malvertising and malvertising-based ransomware.
- A better understanding of the tactics and techniques cybercriminals use to deliver and cover up their malvertising campaigns.
- Tools and solutions to help detect, eliminate, and protect your business.
Speakers: Dana Torgersen, Adam Kujawa & John Pescatore (SANS Analyst)
The Hidden Enemy: Malvertising and Ransomware
Malvertising is increasing in sophistication and prevalence, and often being used to distribute ransomware. According to the FBI, criminals are netting an estimated $325–500 million a year through these scams. But while the FBI is warning of a rise in ransomware, they are at a loss when it comes to how to handle it: “The ransomware is that good,” says Joseph Bonavolonta, the Assistant Special Agent in Charge of the FBI’s CYBER and Counterintelligence Program in its Boston office. “To be honest, we often advise people just to pay the ransom.”
As malvertising-based infections (including ransomware) in businesses increase, questions will arise on who is accountable – ad networks, site owners, or owners of the ad content? If your company is a victim, and the FBI is just advising to pay the ransom, can you begin to seek legal remedy against the ad networks or content owners that were the vector for the infection?
This webinar gives the audience a better understanding of the impact of malvertising and ransomware. It will also tackle some of the biggest misconceptions, latest tactics/incidents, how these attacks are delivered and why your company may be at risk without you even knowing it.
- The growth in malvertising and malvertising-based ransomware
- A better understanding of the tactics and techniques cybercriminals use to deliver and cover up their malvertising campaigns
- Tools and solutions to help detect, eliminate, and protect your business
Securing the Internet of Old Things (IoOT)
Attack surfaces continue to grow, especially as businesses add endpoints and permit new Internet of Things (IoT) to connect to their network. That’s why it’s more important than ever to evolve security to meet today’s changing device and threat landscapes. Join Malwarebytes and G.W. Ray Davidson with SANS Institute as we drill down deeper on recent findings from the SANS 2016 Endpoint Security Survey.
Attend this webinar to learn:
- How time plays a critical factor in your incident response capabilities
- The importance of focusing on IoOT as well as IoT
- How you can prevent malicious attacks and simplify remediation efforts
Endpoint Security Survey 2016: The Evolving Definition of Endpoints
The SANS 2016 survey attempts to define what an endpoint is and explore what types of endpoints are most targeted and why. This webcast will present the first half of the survey results, which are presented in a two-part webcast. It focuses on the evolving definition of endpoints and how that influences endpoint security today.
Attendees will learn:
- The types of devices respondents are connecting to their networks and whether or not theyre considered endpoints that need protection policies
- The types of endpoints are actually covered by organizational policies and tools
- The types of endpoints being breached most often and what breach types are on the horizon
- How long it takes to disinfect an endpoint completely and whether or not organizations know they’ve removed every artifact
Surviving 2016: Protecting Your Business From Advanced Cyber Threats
While traditional security practices still apply in today’s threat landscape, the advanced threats seen in 2015 make it clear that the basics are no longer enough to protect your company. With that in mind, join us as we highlight 10 tips for surviving this year—focusing on what to do and what not to do--to prevent cybercrime in 2016.
2015: The Year of the Flash Zero-Days
Throughout 2015, there seemed to be a never ending exploit of Adobe Flash. Every time a patch was released, cybercriminals found another security hole. And IT admins everywhere struggled to keep pace with the patches. Who knows what the zero-day exploits will be in 2016? But if history is any indication, the proliferation of exploits will continue and leave your employees at risk even while using the programs they trust. Attend this webinar to watch our Malware Intelligence team break down this year's Flash zero-days and learn steps you can take to ensure your business has a secure 2016.
Launch, Detect, Evolve: The Mutation of Malware Webinar
In order to hit their targets, malware developers need to constantly evolve their tactics. This evolution is frequently done in very small incremental changes to known malware attacks. Today, malicious developers know their malware has a short half-life before detection. In order to optimize their efforts, cyber criminals now modify their "products" just enough to evade detection a little bit longer.
Join this intensive webinar to learn:
- New malware tactics researchers and analysts are confronting on a daily basis
- How cyber criminals are using Crypters to evade detection
- What you can do to proactively protect your business from future challenges
Speakers: Adam Kujawa, Head of Malware Intelligence, Malwarebytes
Psychological Warfare: How CyberCriminals Mess With Your Mind
Today's cyber attacks utilize themost complex threat technologies to infiltrate users' computers. Yet much ofthe danger actually lies outside of the code. When attackers combine atechnological attack with psychology—a social engineering tactic similar toadvertising—their reach and effectiveness increases greatly. While most of thesecurity industry is focused on employing new monitoring systems and patchingsecurity holes, at the end of the day, the ultimate target for cyber criminals is the users themselves.
Your Layered Security Defenses are Riddled with Holes...
As attacks became increasingly diverse, numerous and sophisticated, organizations need to take a multi-layered approach to security that goes well beyond traditional endpoint anti-virus and other point solutions. In this webcast, independent information security expert, Kevin Beaver, and Adam Kujawa, Head of Malware Intelligence with Malwarebytes will discuss the holes in a typical layered security approach, share stories, and outline specific technical, procedural, and human defense measures you have to have in order to have a truly successful information security program.
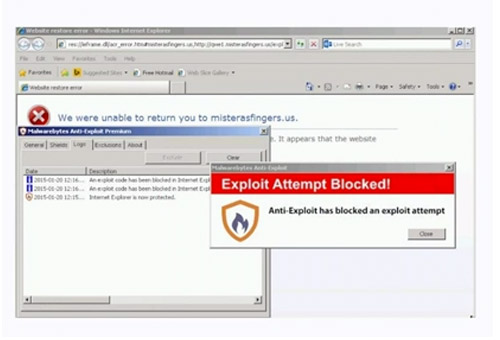
Understanding Zero-Day Attacks and Gaining Control
Zero-days are no longer only used in targeted attacks or by nation states. Mainstream exploit kits are also leveraging them to distribute some of the most vicious malware, such as ransomware. The threat is real and the business risks are immeasurable. In this webcast, independent information security expert, Kevin Beaver, and Jerome Segura, Sr. Security Researcher with Malwarebytes will discuss the big-picture challenges and solutions associated with zero-day exploits and malware against the enterprise. You'll learn specific ways to address your zero-day risks along with how to effectively block and respond to exploit attempts on your network in order to minimize the impact to your business.
An Inside View of a Zero-Day Campaign
At a recent SC Congress eSymposium, Malwarebytes' malware crushing experts delivered an insightful look inside a zero-day malware attack campaign. Since traditional anti-virus approaches leverage lists of known malware to protect against attacks, they can become minimally effective at protecting against zero-day campaigns which are being introduced into the cyber ecosystem for the first time.
Exploits: How they work and how to crush them
Audience: Geared for the IT administrator, but open to anyone interested in cyber security.
What are exploits? How do they work? What makes them so dangerous? And what can be done to protect your users and network against exploit-based attacks? Learn this and more as Malwarebytes researchers tackle one of the most dangerous forms of cyber attack facing businesses today. The webinar will close with a live Q&A session, so you can have your questions answered directly.